A quick visualization with iam.lama from my notes on the Navigate25 keynote by Mark McClain.
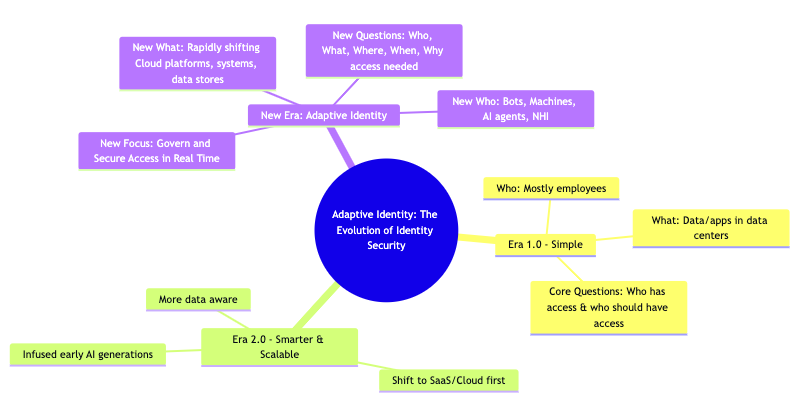
The Evolution of Identity Security (Adaptive Identity): We’re entering a new era that goes beyond employee-only 1.0 models to securing access in real time—where identities now span bots, AI agents, and dynamic cloud environments.
The Current Identity Crisis: Enterprises are facing identity as the primary attack surface. The scale, rise of non-human identities, and the speed of threats make static models obsolete and demand adaptive, AI-driven approaches.
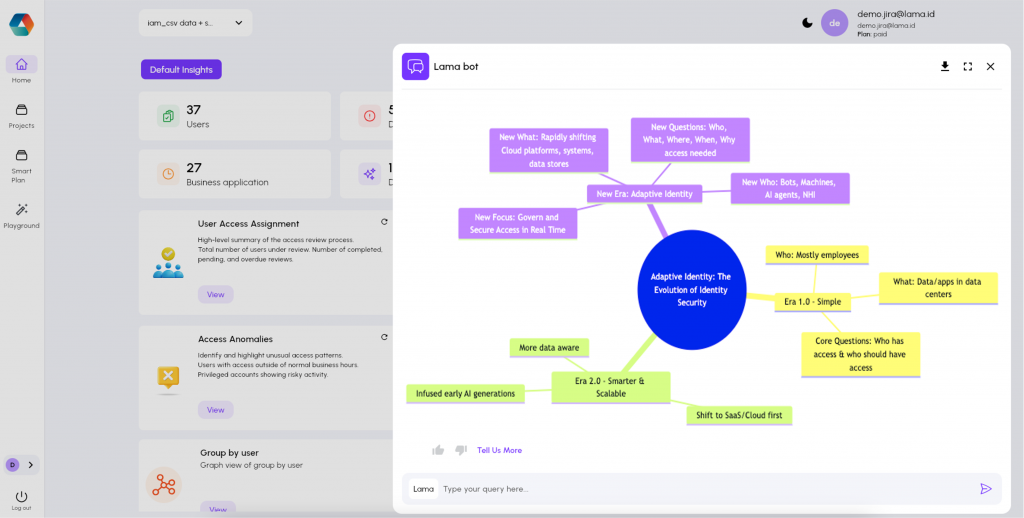
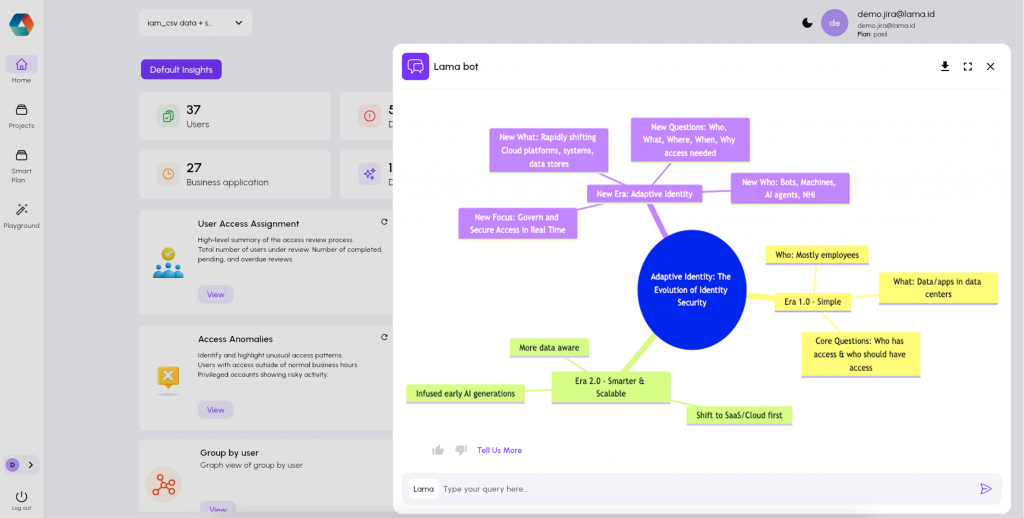
Adaptive Identity: The Evolution of Identity Security
Adaptive Identity represents an evolution of Identity Security, moving from a reactive and static set of controls to a proactive, dynamic, and strategic approach to enterprise security.
Era 1.0 – Simple
The early era of identity security was relatively simple.
- Who: The identity being managed was mostly employees.
- What: The resources being accessed (the “what”) were mostly data and applications located in the organization’s data centers.
- Core Questions: During this time, SailPoint focused on answering three core questions, primarily: “Who has access to what?” and “Who should have access to what?”.
Era 2.0 – Smarter & Scalable
Roughly a decade later, the industry transitioned into the next era, incorporating lessons learned from thousands of implementations.
- Shift to SaaS/Cloud first: Identity security offerings were brought into the realm of SaaS (Software as a Service).
- Infused early AI generations: This era began to infuse early generations of AI.
- More data aware: Identity management became much more data aware.
- Outcome: This shift resulted in a smarter, more scalable form of identity security.
New Era: Adaptive Identity
The current transition is considered stepping into yet another new era, which is referred to as Adaptive Identity.
- New Focus: Govern and Secure Access in Real Time
- It is no longer enough to govern access. The imperative is to secure access in real time, all the time.
- Access to critical information is granted, monitored, and managed dynamically based on policy and context.
- New Who: Bots, Machines, AI agents, NHI
- The definition of “who” has expanded significantly.
- It includes bots and machines, AI agents.
- The volume of non-human identities (NHI) is rapidly exploding. Non-human identities now overmatch human identities by some 45 to 1 in enterprise environments.
- New What: Rapidly shifting Cloud platforms, systems, data stores
- The “what” (resources accessed) is no longer a confined list of applications within the data center. It is now a rapidly shifting mix of cloud platforms, systems, and data stores.
- New Questions: Who, What, Where, When, Why access needed
- Complexity has been added because organizations now must understand not just the “who” and the “what,” but also the “where and when and why does that access need to happen”.
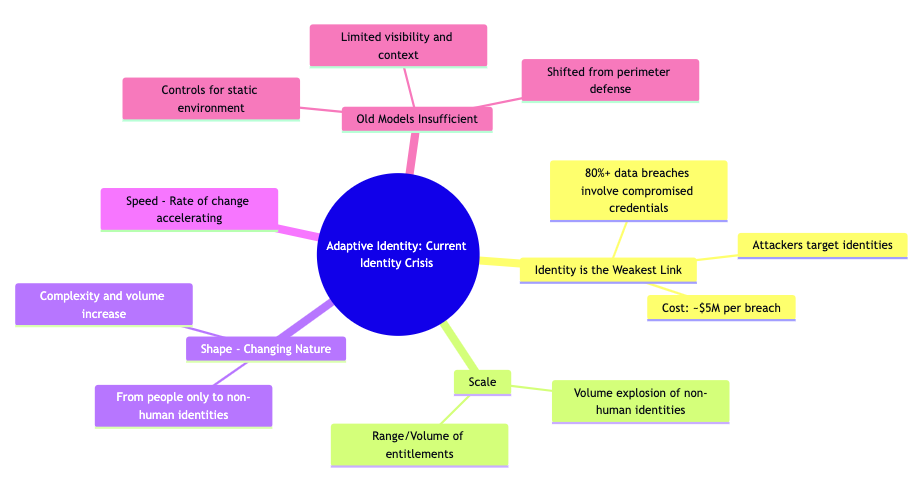
Adaptive Identity: Current Identity Crisis
Organizations are facing an identity crisis due to the explosion of the threat landscape, characterized by challenges in scale, shape, and speed. This shift mandates an evolution beyond traditional identity governance to a new era called Adaptive Identity.
Identity is the Weakest Link
Identity has become the most vulnerable element in enterprise security, acknowledged by both organizations and attackers.
- 80%+ data breaches involve compromised credentials. This illustrates that attackers are not kicking the front door in, but rather abusing trust.
- Cost: ~$5M per breach Identity-related incidents are costing companies approximately $5 million per breach.
Scale
- The sheer magnitude of entities requiring management and protection contributes significantly to the current crisis. Machine identities now overmatch human identities by some 45 to 1 in enterprise environments.
- The increasing scale also includes the range and volume of entitlements those identities are accessing.
Shape – Changing Nature
- The “shape” refers to the changing nature of the identity landscape. Now, the “who” includes bots and machines, AI agents and NHI.
- This transformation results in more complexity and more volume in the identity landscape.
Speed – Rate of change accelerating
- The rise of AI agents is projected to massively accelerate this identity threat, making it even more vital to rethink enterprise protection.
Old Models Insufficient
- Limited visibility and context and often didn’t really understand context.
- Controls for static environment
- Shifted from perimeter defense to identity is now the new perimeter.
- The current approaches to enterprise security are no longer fully effective.